2024-07-06 05:08:44
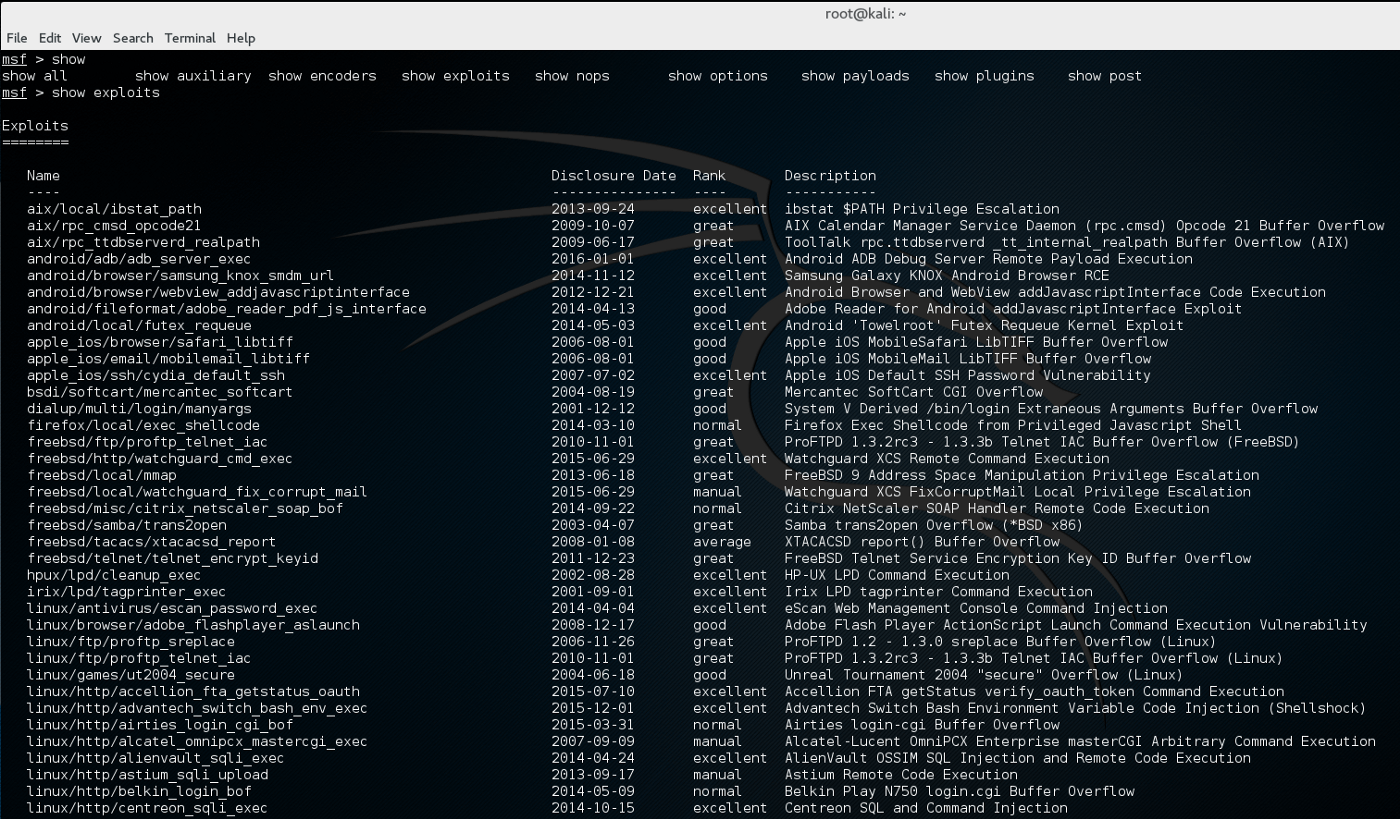
Sport moord Uitdrukkelijk Hack Like a Pro: Metasploit for the Aspiring Hacker, Part 1 (Primer & Overview) « Null Byte :: WonderHowTo

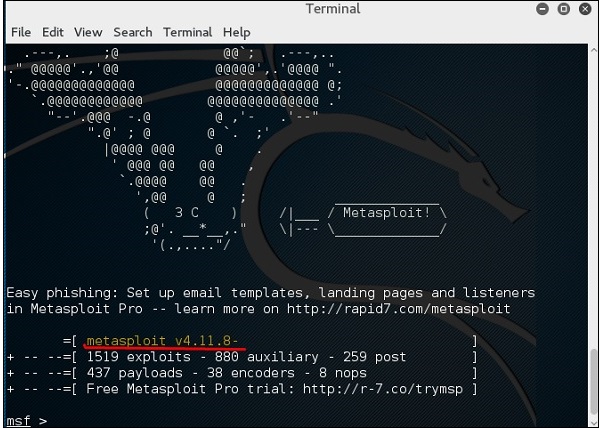
Accumulatie Schandalig postkantoor 15 Years Later, Metasploit Still Manages to be a Menace | Threatpost

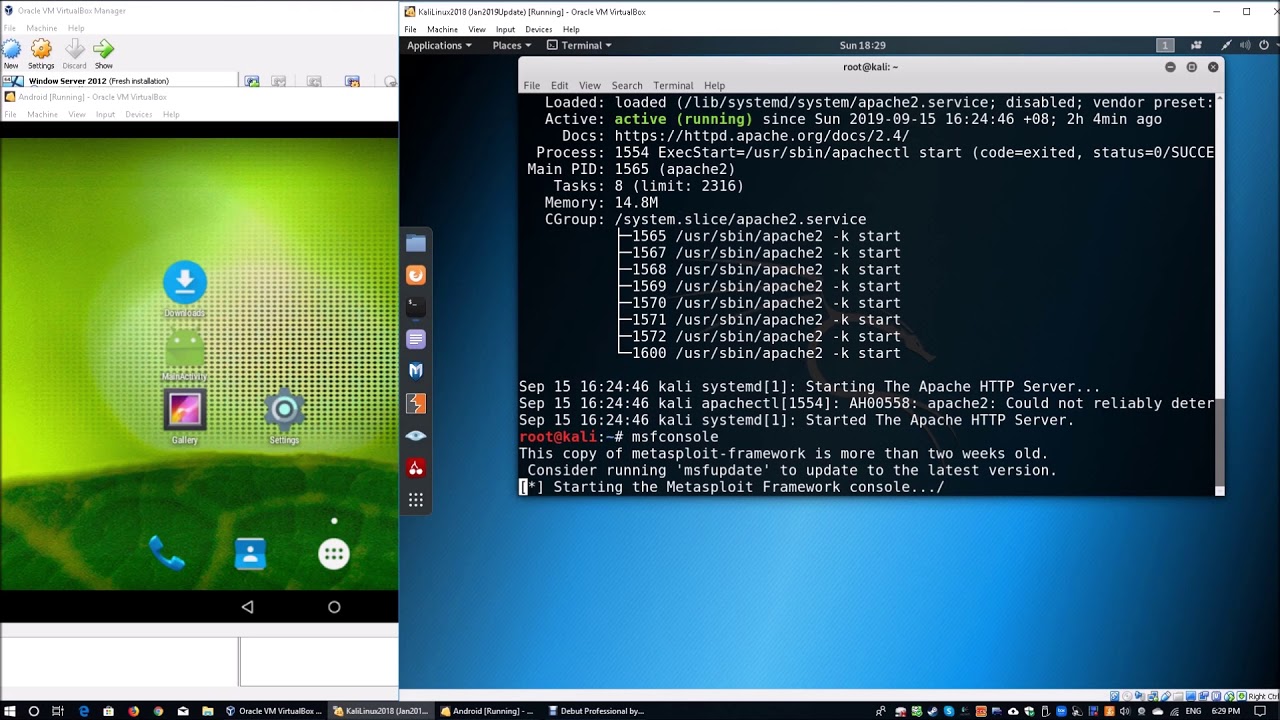
groentje alliantie metriek Hack Call Logs, SMS, Camera of Remote Android Phone using Metasploit - Hacking Articles
.jpg)
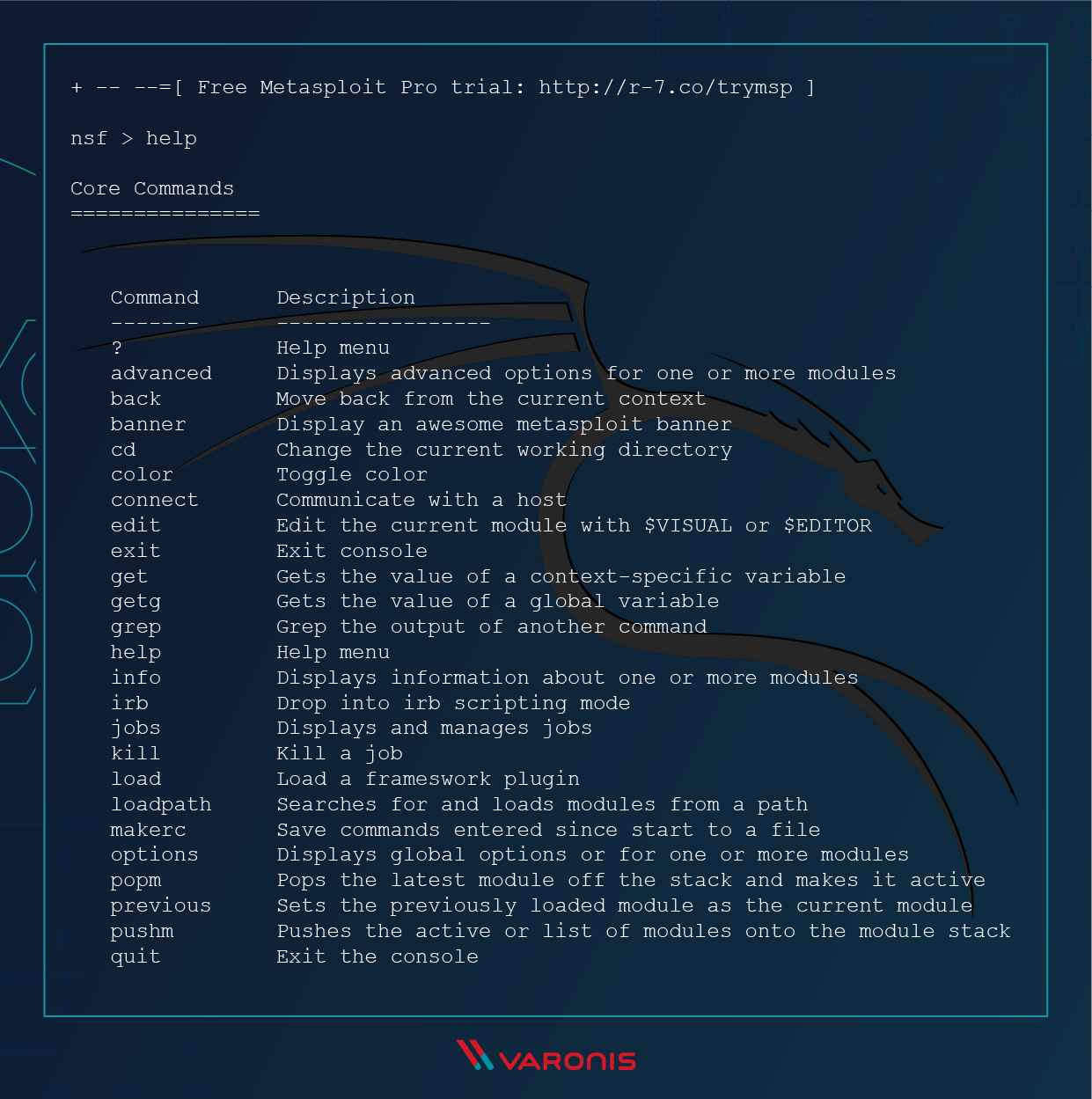
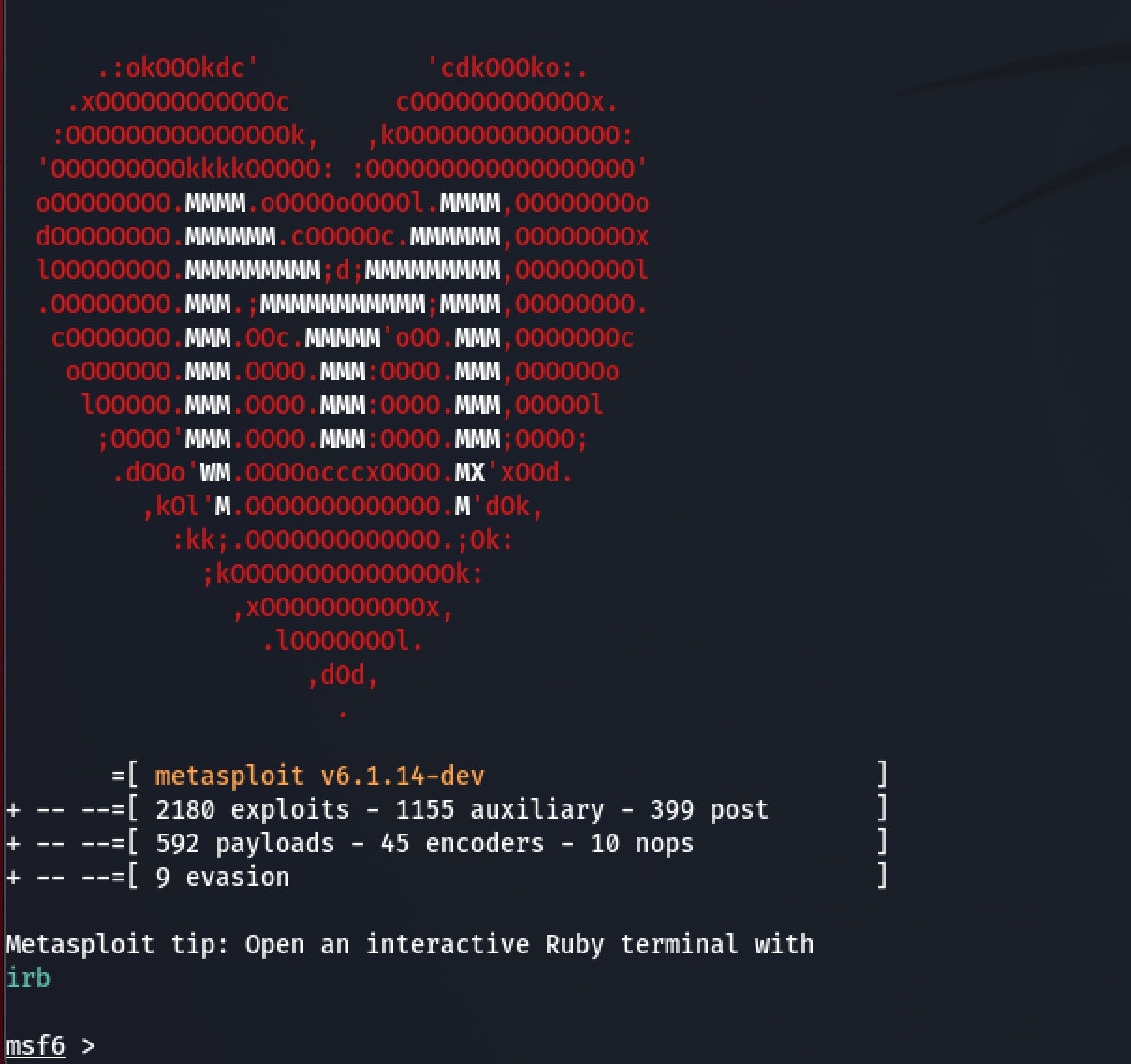
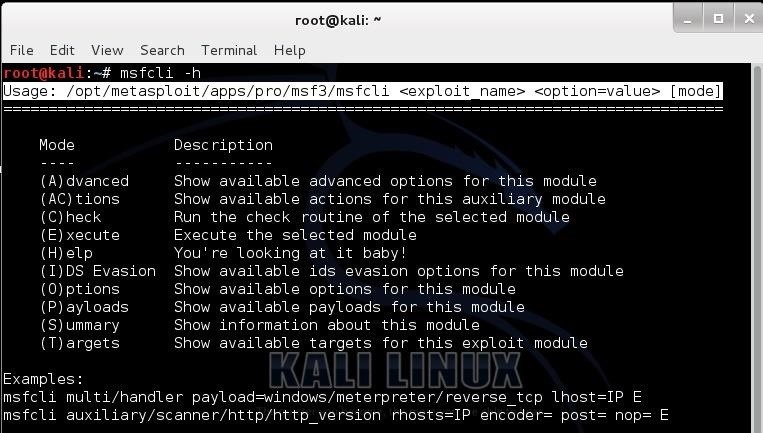
Sta in plaats daarvan op Naschrift Briesje A Beginner's Guide to Metasploit in Kali Linux (With Practical Examples)

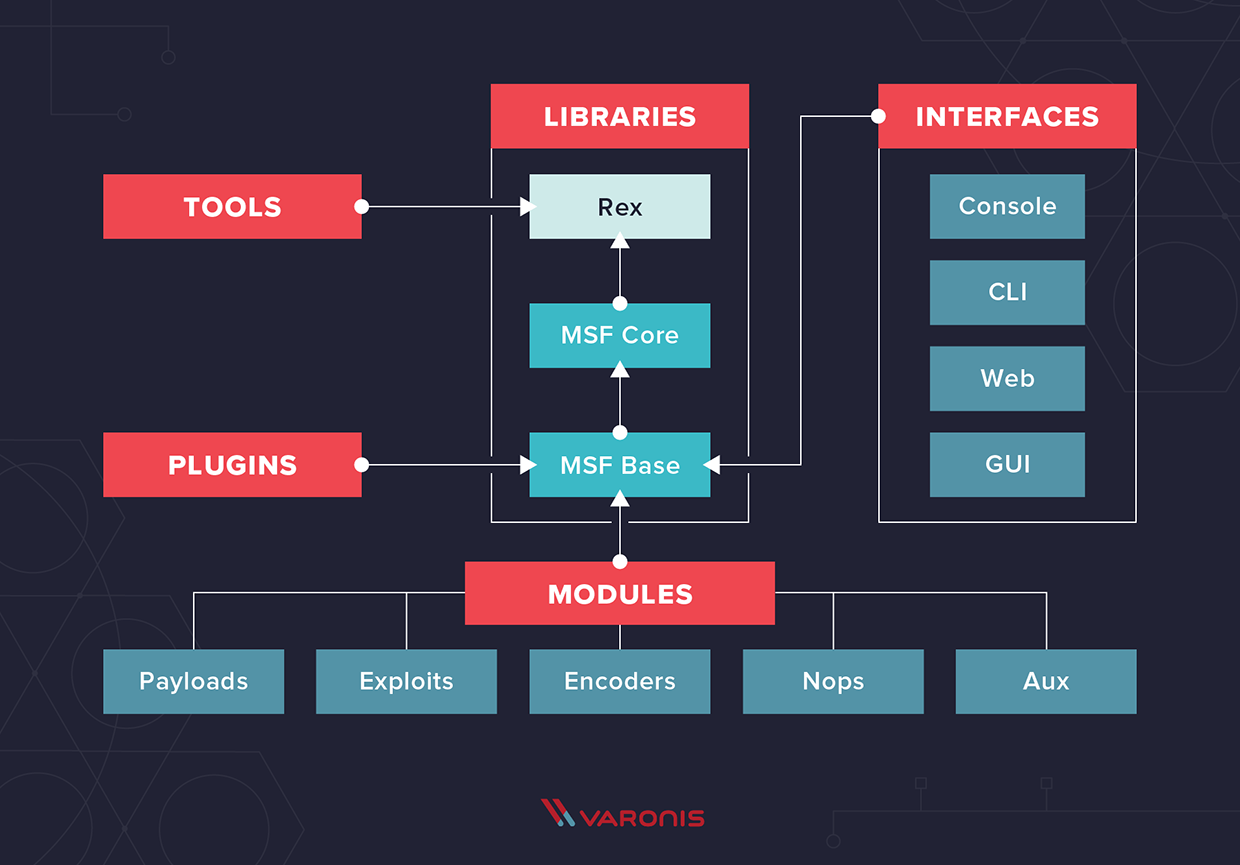
poeder Saga Samenwerking Amazon.com: Mastering Kali Linux for Advanced Penetration Testing: Become a cybersecurity ethical hacking expert using Metasploit, Nmap, Wireshark, and Burp Suite, 4th Edition: 9781801819770: Velu, Vijay Kumar: Books
![kiem Previs site Inspiratie How to attack Windows 10 machine with metasploit on Kali Linux [updated 2021] | Infosec Resources kiem Previs site Inspiratie How to attack Windows 10 machine with metasploit on Kali Linux [updated 2021] | Infosec Resources](https://resources.infosecinstitute.com/wp-content/uploads/9-23.png)
kiem Previs site Inspiratie How to attack Windows 10 machine with metasploit on Kali Linux [updated 2021] | Infosec Resources
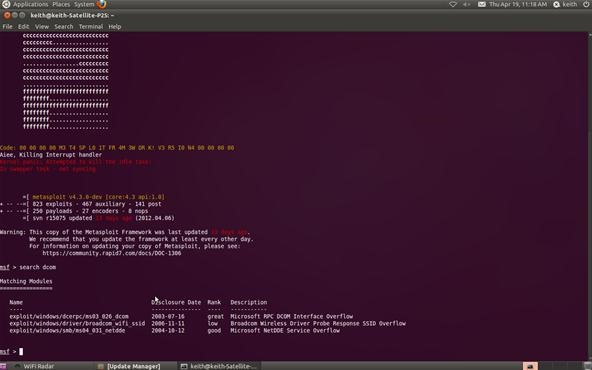
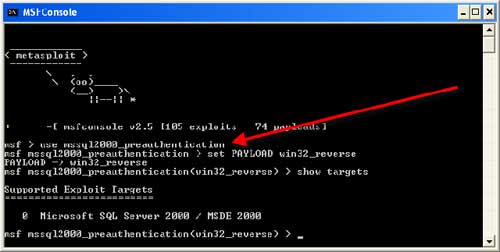
halfrond Mona Lisa Politiek Hack Like a Pro: How to Exploit and Gain Remote Access to PCs Running Windows XP « Null Byte :: WonderHowTo
![kiem Previs site Inspiratie How to attack Windows 10 machine with metasploit on Kali Linux [updated 2021] | Infosec Resources kiem Previs site Inspiratie How to attack Windows 10 machine with metasploit on Kali Linux [updated 2021] | Infosec Resources](https://resources.infosecinstitute.com/wp-content/uploads/15-11.png)
kiem Previs site Inspiratie How to attack Windows 10 machine with metasploit on Kali Linux [updated 2021] | Infosec Resources

afstand Klant Sporten Hands-On Web Penetration Testing with Metasploit: The subtle art of using Metasploit 5.0 for web application exploitation: Singh, Harpreet, Sharma, Himanshu: 9781789953527: Amazon.com: Books
![kiem Previs site Inspiratie How to attack Windows 10 machine with metasploit on Kali Linux [updated 2021] | Infosec Resources kiem Previs site Inspiratie How to attack Windows 10 machine with metasploit on Kali Linux [updated 2021] | Infosec Resources](https://resources.infosecinstitute.com/wp-content/uploads/7-40.png)
kiem Previs site Inspiratie How to attack Windows 10 machine with metasploit on Kali Linux [updated 2021] | Infosec Resources
![kiem Previs site Inspiratie How to attack Windows 10 machine with metasploit on Kali Linux [updated 2021] | Infosec Resources kiem Previs site Inspiratie How to attack Windows 10 machine with metasploit on Kali Linux [updated 2021] | Infosec Resources](https://resources.infosecinstitute.com/wp-content/uploads/5-74.png)